Eliminate all files and remove malware! The number one decontamination solution in the domestic market.
This is a solution that emphasizes the "possibility" that files may contain malware and sanitizes (neutralizes) all target files coming from outside the organization through various channels such as email and the web. - Sanitizes (neutralizes) all target files to block targeted attacks - Easy to implement as a SaaS cloud service - Achieves whitelist-based neutralization to respond to unknown threats
Inquire About This Product
basic information
【Supported Files】 Microsoft Office Files - Excel, PowerPoint, Word, RTF, Visio 2013 and later - Identify and sanitize macros and embedded objects Adobe PDF Files - PDF - Maintain text copy and search functionality after sanitization Image Files - BMP, GIF, WMF, EMF, PNG, JPG, JPEG, TIFF, TIF, WDP - Perform file analysis at the pixel level Email Attachments - EML, MSG, ICS - Sanitize email attachments Compressed Files - ZIP, TAR, RAR, 7Z, GZIP, GZ - Support for multi-compressed files - Re-compression possible after sanitization Video and Audio Files - AVI, MP4, MPEG, MPG, WMV, M4A, etc. AutoCAD Files JWW CAD Files SFC CAD, P21 CAD Files JustSystems Ichitaro Files *For more details, please contact us.
Price information
Please contact us.
Delivery Time
※Please contact us.
Applications/Examples of results
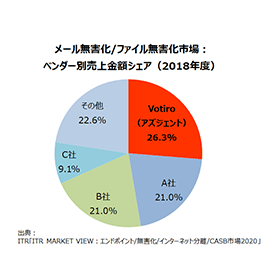
No. 1 in domestic market share for 7 consecutive years in the email/file sanitization market * This refers to Votiro's sanitization solutions, VOTIRO Disarmer and VOTIRO Secure File Gateway. * This is based on sales revenue share from 2016 to 2022. * Source: "ITR Market View: Endpoint/Micro-Segmentation/Sanitization/Web Isolation/CASB/CNAPP/XDR/ZTNA Market 2024," researched in July 2023.
catalog(1)
Download All CatalogsNews about this product(2)
Company information
Azujento is a security solutions company that provides various internet security products and services. We handle a range of security products, including security appliances for SCADA systems that protect industrial control systems and code hardening tools that prevent reverse engineering. We also offer vulnerability assessment services to check for vulnerabilities in network devices, operating systems, and servers.