1~45 item / All 46 items
Displayed results
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
Before making an inquiry
Download PDF1~45 item / All 46 items

Medical institutions handle highly sensitive personal information, such as medical history. While measures to prevent information leaks remain a crucial issue, there has been a recent increase in cyberattacks. The entry point for these attacks is often the remote maintenance lines prepared for handling issues. In this blog, we will provide a detailed explanation of the current security situation surrounding medical institutions and potential solutions, incorporating case studies from hospitals. [Contents] 1) The current security situation surrounding medical institutions 2) Case Study (Initiatives at Hospital A) <Challenges> Remote maintenance lines are a "security loophole" <Measures> Establishing access control and monitoring systems with SecureCube Access Check <Effects> Streamlining remote maintenance-related tasks and reducing the workload of personnel 3) Achieving a safe and secure society with SecureCube Access Check *For more details, please refer to the related links.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
Recently, the use of cloud storage has become common. There are many free options available, leading to a diverse range of choices. On the other hand, when it comes to corporate use, there are concerns about security that need to be addressed. This column explains the essential knowledge and security considerations that corporations should keep in mind when choosing cloud storage. [Contents] ■ Is it okay to use free cloud storage for free? ■ Points to consider regarding collaboration platform-type cloud storage ■ File sharing for administrators who absolutely do not want to fail ■ Services suitable for simple file transfer and sharing for corporations *You can view the detailed content of the blog through the related links.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
When choosing a corporate service for secure file sharing, cloud storage has recently become a popular option. However, if used inappropriately for its intended purpose, it can expose you to security risks. This column will explain the risks and solutions associated with using cloud storage for corporate file sharing. [Contents] ■ Issues with using cloud storage for file sharing - Cloud storage that retains data indefinitely - Can easily become a chaotic "lawless zone" if left unattended - Services that are continuously used may change ■ What services can achieve safe file sharing for corporations *For more details, please refer to the related links.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
What kind of file transfer service is suitable for handling highly confidential information such as personal data and technical information? In this column, we will explain the points to consider when selecting a file transfer service with a focus on security, aimed at corporate administrators seeking high security. [Contents] ■ Do not choose based on comparison tables ■ Create a unique checklist for your company, not a generic comparison table ■ Let's take a look at other companies' checklists ■ What is the file transfer service with a high security level that has been continuously chosen by the financial industry? *You can view the detailed content of the blog through the related links.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
Email misdelivery is mostly due to minor human errors. On the other hand, it is always cited as a leading security incident. It is a highly risky issue that can lead to serious accidents. This column explains what to consider when implementing measures against email misdelivery, effective countermeasures, and how to respond when a misdelivery actually occurs. [Contents] ■ Why does email misdelivery continue to happen? ■ What are effective measures against misdelivery? ■ What to do when a misdelivery occurs *You can view the detailed content of the blog through the related links.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
Is it acceptable to use cloud storage for file sharing in business? This column explains the correct way to choose cloud storage and the risks to consider, aimed at IT personnel who are struggling with selecting file-sharing tools. Additionally, it covers the fundamental knowledge of file servers, cloud storage, and file sharing that IT personnel should be aware of, explaining it from a historical perspective. [Contents] ■ What is the origin of cloud storage? - The dawn of on-premises file servers - The emergence and spread of the cloud - Is file sharing with cloud storage problematic? ■ Recommended tools for simple file transfer and sharing *You can view the detailed content of the blog through the related links.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
File transfer services come in various paid options for businesses, and there are also many free services available for individuals. Additionally, there is a noticeable opinion that "for file transfers, shared services like online storage are sufficient." So, which option is the correct one to use? This column will provide a detailed explanation from basic knowledge to recommended services. [Contents] ■ Is it okay to use free services? ■ What is the difference between file transfer and file sharing? - Characteristics of file sharing services - Characteristics of file transfer services - Which is more suitable for corporate use? ■ High-security file transfer services that receive strong support from the financial industry *You can view the detailed content of the blog through the related links.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
The spread of file sharing has brought renewed attention to "IRM (Information Rights Management)." IRM is a system that encrypts files and grants operation permissions to individual users, while also tracking usage at the destination. In this column, we will explain the basics of IRM, the background that necessitates it, and points to consider when implementing it, as its importance has been increasingly recognized with the rise of cloud storage and other technologies. [Contents] ■ The background for the attention on IRM and what IRM can do ■ The features of IRM that allow management of files even after sending *Detailed content of the blog can be viewed through the related links.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
The handling of My Number information (specific personal information) is strictly regulated by law. On the other hand, there are many means of transfer besides mailing and face-to-face interactions. As a business, how can we comply with the rules while also improving efficiency? NRI Secure offers a free guidebook that clearly summarizes key points to consider. Please feel free to download it. *This column includes excerpts from the guidebook. [Contents] ■ Is it permissible to attach files to emails? ■ What are the points to be cautious about when outsourcing? ■ Three essential conditions for using file transfer services *You can view more detailed content on the blog through the related links. *For more information, please refer to the PDF document or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
Information leaks and system outages due to cyber attacks and internal misconduct. As these threats increase, it is essential for system administrators to thoroughly manage high-privilege IDs (privileged IDs) to prevent serious incidents. "Access Check Essential" is a solution that focuses on three essential functions for controlling access to privileged IDs (access control, log acquisition and storage, audit support) and offers them at a low price. Since complex operational design and configuration are not required, you can quickly take the first step in privileged ID management in a short period and at a low cost. It is ideal to start with the minimum necessary controls for robust privileged ID management. 【Benefits】 ◎ You can immediately start access control and evidence acquisition. ◎ It minimizes the operational burden on administrators. ◎ It reduces the initial implementation costs. ★ We are currently offering explanatory materials summarizing basic knowledge about privileged ID management for new system administrators. * For more details about this solution, please refer to the related links.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
A VDR (Virtual Data Room) is a space for storing and sharing digital documents in a virtual environment, such as the cloud. Originally, it has been used in limited industries and applications, such as the medical field and M&A (mergers and acquisitions). However, recently, companies in other industries seem to be considering its implementation. What are the differences and advantages compared to cloud storage and file-sharing services? This article provides a detailed explanation of the basic knowledge of VDRs, their origins, and key points to consider before implementing them. [Contents] ■ What is a VDR (Virtual Data Room)? ■ VDRs used for special purposes ■ In what scenarios can VDRs be used across industries? ■ How to prevent mismatches with VDR services? *For more details, you can view the related links. *You can download materials for the secure file exchange service "Crypto-bin." *For more information, please refer to the PDF materials or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
In Japan, the leading cause of security incidents is consistently attributed to email misdelivery. The risks are clear, yet cases of using email for the exchange of personal information continue unabated. This must be a headache for security personnel in companies. In this article, we will revisit the issues with email, clarify the background of incidents and accidents, and identify areas for improvement. Additionally, we will introduce appropriate alternatives for sending personal information instead of email. [Contents] ■ Email misdelivery ranks as the "No. 1 incident/accident that occurred in the past year" ■ Why is email not sufficient? ■ The misconception that "encryption makes it safe" ■ What services are acceptable for the transfer of personal information? ■ Safely handling personal information: Corporate file transfer service "Crypto-bin" *You can view the detailed content of the blog through the related links. *You can download materials for the secure file exchange service "Crypto-bin." *For more information, please refer to the PDF materials or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
We would like to introduce a case study of ONE COMPATH Co., Ltd., which operates one of the largest electronic flyer services in Japan, implementing "SecureCube Access Check." In their services, the company utilizes this product to appropriately manage permissions during infrastructure setup, application testing, and release operations. Even after transitioning to a telework environment due to the impact of the COVID-19 pandemic, they have upgraded their systems and are effectively managing the permissions of administrators working from home. 【Case Overview】 ■ Implementing Company: ONE COMPATH Co., Ltd. ■ Implemented Product: SecureCube Access Check ■ Implementation Benefits ・Operations can continue smoothly even during telework ・Reduction in the workload and man-hours for management staff *For more details, please refer to the related links or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
We would like to introduce a case study of Idemitsu Kosan Co., Ltd., which has implemented "SecureCube Access Check" for centralized management of personal IDs and logs. One of the features of the "Financial Instruments and Exchange Act," which was applied starting in the fiscal year 2008 in accordance with the U.S. Sarbanes-Oxley Act (SOX), is the clear incorporation of internal controls related to information systems. As a major company in oil refining and sales, Idemitsu Kosan has adopted this product as a measure to manage access to its information system infrastructure, achieving efficient security management economically. 【Case Overview】 ■ Client: Idemitsu Kosan Co., Ltd. ■ Product Implemented: SecureCube Access Check ■ Implementation Effects: - Strengthened security regarding access to numerous servers in the information system infrastructure - Significant cost reduction - Achieved efficient operations *For more details, please refer to the PDF document or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
We would like to introduce the case of Tokyu Card Co., Ltd., which implemented the high-privilege (privileged ID) management solution "SecureCube Access Check." In 2015, the company began efforts to establish a more secure card usage environment in compliance with the security standards for credit card information protection, PCI DSS. They introduced our product as their ID management tool, further strengthening their security management system and enhancing security awareness. 【Case Overview】 ■ Client: Tokyu Card Co., Ltd. ■ Product Implemented: SecureCube Access Check ■ Implementation Effects - Achieved strong access control required by PCI DSS - Significantly improved security awareness across the organization *For more details, please refer to the PDF document or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
We would like to introduce a case study of Internet Initiative Japan Inc., which has implemented the privileged ID access management tool "SecureCube Access Check." The company adopted this product in 2014 to integrate management of internal access to approximately 27,000 nodes of servers located on-premises and in a private cloud. This has achieved robust information security based on strict and flexible access control. 【Case Overview】 ■ Client: Internet Initiative Japan Inc. ■ Product Implemented: SecureCube Access Check ■ Implementation Effects - Complete digitization of access management - Significant improvement in the accuracy and efficiency of audit tasks *For more details, please refer to the PDF document or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
We would like to introduce a case study where Tower Records Inc., which provides music-related products and services, has implemented the cloud-based privileged ID access management solution "Cloud Auditor by Access Check." The company migrated its on-premises privileged ID management tool for its e-commerce site to this product. This has resulted in significant efficiency improvements in system audit compliance and an enhancement in security levels. Additionally, in terms of operations, they have been freed from the cumbersome tasks of regular version upgrades, allowing them to create a system foundation for future business development. 【Case Overview】 ■ Client: Tower Records Inc. ■ Product Implemented: Cloud Auditor by Access Check ■ Implementation Effects ・Easily meets stringent audit compliance levels ・Operational tasks have been drastically reduced to nearly zero *For more details, please refer to the PDF document or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
We would like to introduce a case study of the implementation of "Crypto Delivery" at Mitsubishi Pencil Co., Ltd. The company utilizes this product in their workflow for adding designs to writing instruments to ensure safe and reliable data transmission. Previously, large files that could not be sent via email were copied to MO and exchanged by mail, which could take several days to complete one process. However, after introducing this product, it has become common to complete tasks within the same day. [Key Points] - There is anxiety about not being able to confirm whether the email has "definitely been received," along with concerns about the leakage of commercial design information. - Large files can be sent and received safely and reliably without the need for system development, making it relatively inexpensive to use. - It is a highly reliable system that is web browser-based, making it easy to operate and increasing business speed. *For more details, please refer to the related links or feel free to contact us.*
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
We would like to introduce a case where "Crypto Delivery" was implemented at Aozora Bank, Ltd., which provides unique and highly specialized financial services to its customers. In order to conduct file transfers to clients and others more securely, the bank adopted this product in 2018. Not only does it encrypt and send important data such as customer information, but it also implements advanced security management systems required by financial institutions, including audit functions in case of emergencies. 【Key Points】 ■ Sends all documents, including large files, encrypted with TLS ■ Achieves secure file transfer suitable for financial institutions ■ In addition to enhancing security, strengthens and renews the "file transfer system" from the perspective of business control ■ Response exceeded expectations after implementation, already expanded to 22 internal departments and 3 group companies *For more details, please refer to the PDF document or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration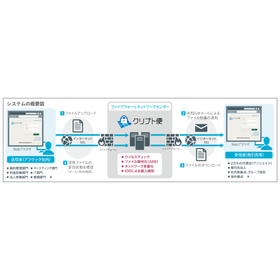
To Aflac Life Insurance Co., Ltd., which provides insurance products and services, we would like to introduce a case study of the implementation of "Crypto Delivery." In conjunction with the enforcement of the Personal Information Protection Law, the company adopted our product as a more secure method for the transfer of customer information and other data. They completely eliminated the use of CD-ROMs and USB drives, significantly minimizing the risk of information leaks while also achieving a substantial reduction in the operational burden of media management. 【Key Points】 - Complete elimination of data transfer via physical media - Reduction of information leakage risks and media management burdens - Encryption features that meet the necessary security levels for insurance companies - Implementation of the AES encryption standard, which is the U.S. encryption standard *For more details, please refer to the PDF document or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
We would like to introduce a case study of the implementation of "Crypto Delivery" at Dai-ichi Life Card Service Co., Ltd., which is engaged in payment collection services and credit card business. In the payment collection business, they handle approximately 1.7 million transfer operations annually for about 1,300 companies, requiring extremely high information security for the vast amount of personal information exchanged. To address this, the company has implemented the "Crypto Delivery Autopilot Option," achieving a more robust personal information protection system and significant cost reductions through automation of operations. 【Key Points】 - Elimination of the need to manage physical media for data transmission that was previously outsourced, resulting in an annual cost reduction of 2 million yen. - Direct integration of business systems with Crypto Delivery via API, greatly improving the efficiency of sending and receiving operations. - Reduction in incidents related to physical media, lowering indirect costs of system operations and the psychological burden on staff. *For more details, please refer to the PDF document or feel free to contact us.*
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
We would like to introduce a case study of the implementation of "Crypto Delivery" at NEXCO Systems Co., Ltd., which is responsible for everything from the development to the operation management of core systems. The company received a request from customers to create a more secure file transmission system and proposed our cloud service product. By achieving ID/password integration with the existing internal authentication infrastructure, we significantly streamlined access management for approximately 5,300 accounts while leveraging the cost-effectiveness unique to the cloud, resulting in robust and user-friendly email security. 【Benefits of Implementation】 ■ Enabled single sign-on with the internal authentication infrastructure, securely and efficiently managing ID/password operations for about 5,300 users. ■ Eliminated expenses from the on-premises era, resulting in significant cost savings. ■ Achieved robust and user-friendly email security. *For more details, please refer to the PDF document or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
We would like to introduce a case study of InfoScience Co., Ltd., which has implemented our high-privilege ID (privileged ID) management solution, "SecureCube Access Check." The company has integrated our product with a unified log management tool for managing access and security of servers used by customers of their hosting services. They have achieved secure log management that includes data utilization by collecting and storing various logs generated from system operations, as well as access records, and issuing management reports based on this data. 【Case Overview】 ■Implementation Client: InfoScience Co., Ltd. ■Implemented Product: SecureCube Access Check ■Implementation Benefits ・Centralized management of server logs regardless of the number of servers ・Hybrid operation with both cloud and on-premises is also possible *For more details, please refer to the PDF document or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
We would like to introduce a case study of the implementation of "Crypto Delivery" at Sumitomo Life Insurance Mutual Company. Until now, the company has been exchanging various business information with customer companies using FD and MO, but the process of exchanging information through electronic media has been cumbersome and improvements have been desired from the perspective of information security. Therefore, the company introduced our product starting in January 2015. In addition to reducing the costs and efforts associated with data exchange, they have implemented a system for data transfer that is more efficient and protected by robust security, utilizing features such as the "Closed Group" function, which allows file exchanges only among designated users. 【Key Points】 ■ Utilization of the "Closed Transmission Function" for the exchange of personal information ■ Minimization of the risk of information leakage due to misdelivery ■ Confirmation of advantages in both security and cost aspects *For more details, please refer to the PDF document or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
We would like to introduce a case study of implementing "Crypto Delivery" at ROBOT PAYMENT Inc., which provides payment processing services specialized for subscription-based services. The company used physical media such as USB memory sticks to transfer credit card information between client companies. This made it difficult to respond quickly and raised concerns about the risks of loss and theft. By adopting our product, which complies with the PCI DSS security standards in the credit card industry, they aim to reduce labor and operational costs. 【Key Points】 - Transition from transferring credit card information via USB memory to a speedy online transfer. - Adoption of a service that complies with PCI DSS and has a proven track record with many financial institutions, ensuring high-level security. - Implementation of secure operations through access restrictions limited to specific members and device authentication. *For more details, please refer to the related links or feel free to contact us.*
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
On November 17, 2020, Takeya Hirai, the Minister for Digital Reform, announced at a regular press conference that the government plans to abolish the use of "password-protected zip files" by central government employees when sending documents and other data via email. This issue may evolve into a social problem involving private companies as well, leading to an increase in businesses struggling with essential security measures for file transmission to replace the current PPAP operation. Our blog explains why the PPAP operation is not "encryption that guarantees security levels" and how to ensure security levels. [Contents] - What is a password-protected zip file (PPAP operation)? - Why is the PPAP operation problematic? - Why does the PPAP operation persist? - How should files be sent securely? - Summary *You can view detailed content on the blog through the related links. Please feel free to contact us for more information. *You can download materials for the secure file exchange service "Crypto-bin."
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
In order to prevent the spread of the new coronavirus, many companies are continuing to implement telework. To maintain business operations under telework, there may be situations where important files, such as contracts, invoices, and documents containing customer personal information, are shared using cloud services. However, when using cloud services that have not been utilized before, security concerns may arise. On our blog, we explain the means and challenges of "file sharing" during telework, as well as solutions for IT personnel who are struggling with this issue. [Content Overview] ■ Means and challenges of file sharing in telework ■ Approaches to solving file sharing challenges in telework ■ For corporate file transfer/sharing, use "Crypto-bin" ■ Summary *For more detailed content of the blog, you can view it through the related links. Please feel free to contact us for more information. *You can download materials for the secure file exchange service "Crypto-bin."
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
What are the most threatening events for your company? According to our research, many Japanese companies report that information leakage due to targeted attacks and internal misconduct are the most significant threats they perceive. To protect against these threats, it is necessary to reduce risks through a multi-layered defense that combines various security measures. One of the important countermeasures among these is "proper management of privileged IDs." In our company's blog, we clearly explain the importance of "privileged ID management" and the approaches to it. [Contents] ■ What is a privileged ID? ■ Risks associated with improper management of privileged IDs ■ Incident cases due to inadequate management of privileged IDs ■ Best practices for privileged ID management ■ Conclusion *Detailed content of the blog can be viewed through the related link. Please feel free to contact us for more information. *You can download materials for the privileged ID access management solution "SecureCube Access Check."
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
In recent years, more companies have been adopting and utilizing telework, such as remote work from home. As it allows for effective use of time and location, many people are now seen teleworking not only from home but also from coffee stands in the city and shared offices. In light of the recent COVID-19 pandemic, an increasing number of companies are considering telework as part of their business continuity plans (BCP) in response to natural disasters like extreme weather and incidents. Therefore, on our company's blog, we explain what system administrators should consider when performing their duties remotely as telework becomes more widespread. [Content] ■ Three essential elements for a location-independent system maintenance environment ■ System management during telework using SecureCube Access Check ■ Summary * You can view the detailed content of the blog through the related links. Please feel free to contact us for more information. * You can download materials on the privileged ID access management solution 'SecureCube Access Check'.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
Due to the impact of the COVID-19 pandemic, many companies have adopted telework to avoid contact with others as much as possible. On the other hand, because telework limits face-to-face communication, there are challenges in understanding how other employees, partner company employees, and IT vendors are conducting their work, and whether there are any security issues. In our company's blog, we focus on "privileged ID management," which is used for system maintenance, and we introduce the risks and countermeasures related to the use of privileged IDs in telework. [Content Overview] ■ Challenges of using privileged IDs in telework ■ Key points for managing privileged IDs in telework ■ Examples of utilizing privileged ID management solutions in telework ■ Conclusion *You can view the detailed content of the blog through the related links. Please feel free to contact us for more information. *You can download materials for the privileged ID access management solution "SecureCube Access Check."
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
In recent years, due to the rampant spread of the new coronavirus, companies have been strongly encouraged to adopt telework. While there is a desire to promote telework, there may be individuals who are anxious about how to address security incidents and accidents. Our company's blog focuses on "privileged ID management," a security measure aimed at preventing the leakage of IDs and passwords, which often trigger many security incidents and accidents. We explain the differences in the "methods" of privileged ID management and the selection points for privileged ID products, taking into account their respective advantages and disadvantages. [Contents] ■ Are administrator accounts and root accounts under threat? ■ What is a privileged ID? ■ [Comparison] Differences in methods of privileged ID management products ■ New trends in privileged ID management products ■ Conclusion ■ About SecureCube Access Check *You can view the detailed content of the blog through the related links. For more information, please feel free to contact us. *You can download materials for the privileged ID access management solution "SecureCube Access Check."
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
As the utilization of the cloud progresses, the vague anxieties that many have felt about "using the cloud" are diminishing. However, on the other hand, many companies may still harbor concerns about security, wondering whether they can adequately address issues such as the leakage, loss, or unauthorized access of important data. In our blog, we focus on the user's area of responsibility and introduce methods for managing privileged IDs that users should be aware of when using the cloud. [Contents] ■ Security considerations in the cloud ■ Privileged IDs that should be managed within the user's area of responsibility ■ Examples of tools for managing privileged IDs in cloud usage ■ Conclusion *You can view the detailed content of the blog through the related links. Please feel free to contact us for more information. *You can download materials on the privileged ID access management solution "SecureCube Access Check."
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
In recent years, due to the rampant spread of the new coronavirus, companies have been encouraged to adopt telework. There may have been discussions about how to manage the administrator ID/passwords that were previously used only within the company. How should the management of privileged IDs, which are different from regular IDs, be conducted? In our company's blog, we particularly focus on the "differences in ID management methods" for privileged IDs and introduce key points to consider when selecting privileged ID products, taking into account the advantages and disadvantages of manual operations. [Contents] ■ What are the "differences in ID management methods" for privileged ID management? ■ Let's try using privileged ID management products ■ Conclusion *For more details on the blog content, you can view it through the related links. Please feel free to contact us for more information. *You can download materials for the privileged ID access management solution 'SecureCube Access Check'.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
NRI Secure Insight for 2020 published by NRI Secure. We conducted a "Survey on the Status of Information Security in Companies" targeting companies in Japan, the United States, and Australia, and found significant differences in the understanding and awareness of information security among Japanese companies. In our blog, we explain specific solutions for internal fraud response measures and key points, based on the differences in awareness regarding security controls of outsourced partners and potential cases that may arise. [Contents] ■ Current status and reality of security measures in Japanese companies ■ Cases of information leakage due to internal fraud ■ Three security measures to prevent information leakage due to internal fraud ■ Effective solutions for security measures against information leakage due to internal fraud: "Privileged ID Management" ■ Conclusion *Detailed content of the blog can be viewed through the related links. Please feel free to contact us for more information. *You can download materials for the privileged ID access management solution "SecureCube Access Check."
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
Incidents of information leakage due to internal misconduct continue unabated. Once again, we should review our measures to prevent information leaks by insiders within the organization. Countermeasures against internal misconduct should not only make it technically impossible to commit such acts but also encompass various aspects such as physical management and employee compliance. Our company's blog organizes the perspectives on internal misconduct countermeasures and explains them based on specific examples of measures. Please use this to assist in reviewing internal misconduct countermeasures within your organization. 【Contents】 ■ Introduction ■ About Internal Misconduct ■ Examples of Internal Misconduct Countermeasures ■ Conclusion *You can view the detailed content of the blog through the related links. For more information, please feel free to contact us. *You can download materials for the privileged ID access management solution "SecureCube Access Check."
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
Due to the rapid global expansion of telework in recent years, it has become possible to access areas that were previously protected by boundaries. Additionally, with the recent globalization, companies are interacting with numerous businesses both domestically and internationally, leading to more opportunities to access information from domestic and international data centers and utilize SaaS services. The era where it was sufficient for a company to secure its own security has shifted to a necessity for implementing security measures that span across the supply chain. Our blog focuses on access management and explains best practices for supply chain management. [Contents] ■ What is a supply chain? ■ Threats to the supply chain ■ Best practices for access management ■ Effective products and solutions for access management ■ Summary *You can view detailed content of the blog through the related links. Please feel free to contact us for more information. *You can download materials for the privileged ID access management solution 'SecureCube Access Check'.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
The international security standard "PCI DSS" for businesses handling credit cards is scheduled for a major version upgrade from the current 3.2.1 to 4.0, marking the first update in about eight years. Many businesses and merchants are constantly busy with compliance to PCI DSS. Furthermore, the transition to the new version may cause concern for many. In our blog, we will review the overview of PCI DSS and explain key points for maintaining security levels while streamlining operations from the perspective of access management and log management experts. For those who are about to start working on PCI DSS compliance, please use this as a reference for future-oriented measures. [Contents] ■ What is PCI DSS ■ Reasons why maintaining PCI DSS compliance is difficult ■ How to maintain PCI DSS compliance security standards ■ Summary *Detailed content of the blog can be viewed through related links. *You can download materials for the privileged ID access management solution "SecureCube Access Check."
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
"SecureCube Access Check" is a privileged ID management solution that protects critical systems from attacks with robust access control. It also complies with internal controls such as IT general controls and PCI DSS. It reduces implementation costs with a configuration that does not impact existing systems. Even for large-scale systems, it allows for a small start and early implementation. All functions, from work requests to audits, are provided in one solution. It has been adopted by various customers across industries, including manufacturing, financial institutions, and distribution, and has received high praise for its detailed maintenance and support system unique to in-house development, as well as for feature expansions that reflect customer feedback. 【Features】 ■ Achieves high security with minimal effort ■ Eliminates fraudulent activities in critical systems ■ Streamlines and reduces labor in audit operations ■ Complies with internal controls such as IT general controls and PCI DSS *For more details, please refer to the PDF document or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
This document introduces the proper handling of specific personal information and the means of transferring My Number that corporations can use. It includes explanations of physical and technical safety management measures, as well as the advantages and issues of transfer methods such as email, fax, and registered mail. Additionally, it explains the three essential conditions for file transfer services and the safe and secure collection of My Number using "Crypto Delivery." We encourage you to read it. 【Contents】 ■ Introduction ■ 1. Proper handling of specific personal information ■ 2. Advantages and issues of transfer methods ■ 3. The choice of "file transfer services" ■ Conclusion *For more details, please refer to the PDF document or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
In this document, we will consider the secure transfer of files and introduce approaches to problem-solving through actual case studies. We will provide a detailed explanation of the risks associated with file transfers, including the use of email, the careless use of free services, and the improper handling of My Number. Additionally, we will present case studies from various industries, including Company A, an IT specialist, Company B, which operates in the credit card business, and Company C, a manufacturer. We encourage you to read it. [Contents] ■ Introduction ■ 1. Risks Associated with File Transfers ■ 2. Use Cases by Issue ■ <Reference> Why You Shouldn't Choose Based on Comparison Tables? *For more details, please refer to the PDF document or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
"Crypto Delivery" is a cloud service that facilitates file exchange through a dedicated server equipped with robust security measures. Since it utilizes a web browser, there is no need to build a new system. It offers menus in Japanese, English, and Chinese, allowing for smooth file exchanges with overseas companies. Equipped with high security features unique to information security specialist companies, it is adopted by many businesses, including banks. With "Crypto Delivery," you can safely and easily transition from zip files! ■ No need for dedicated devices or software ■ Combines usability similar to email with security ■ Abundant measures against misdelivery and security ■ Proven track record in companies requiring high security, such as banks
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
This document introduces the four basic steps of privileged ID management that information system administrators should know once they become administrators. Starting with "System Management and Privileged IDs," it details the "Risks Associated with Privileged ID Usage," "Basics of Privileged ID Management," and "Challenges in Privileged ID Management," using diagrams for clarity. When assigned as a system administrator, it is advisable to review whether your company's privileged ID management is implementing these four basic steps. Furthermore, in daily operations, if there are challenges related to management burden, costs, or management accuracy, consider implementing a privileged ID management solution to enhance the overall productivity of system management. [Contents (Excerpt)] ■ Introduction ■ System Management and Privileged IDs ■ Risks Associated with Privileged ID Usage ■ Basics of Privileged ID Management ■ Challenges in Privileged ID Management *For more details, please refer to the PDF document or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
The duties of system administrators require maintaining and operating information systems that support business activities, even in situations where employees cannot come to the office due to natural disasters such as extreme weather or large-scale incidents. This document focuses on the work of system administrators, which is being re-evaluated as part of BCP (Business Continuity Planning) in light of the spread of telework, and outlines three key points to consider when performing these tasks remotely. We encourage you to read it. [Contents (excerpt)] ■ Introduction ■ 1. Three essential elements for a location-independent system maintenance environment - Point 1: Establish a remote access environment - Point 2: Reassess the application flow using paper media - Point 3: Record and verify the tasks performed *For more details, please refer to the PDF document or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
We support the implementation of the 'SCADAfence Platform', a solution for monitoring and detecting cyber attacks on industrial IoT systems. The 'SCADAfence Platform' can be integrated into existing networks through passive network monitoring using mirror ports and networks, and it has a proven track record of deployment in large-scale sites, including factories with over 20,000 devices, primarily in the automotive and electronics sectors in Europe and the United States. 【Features】 ■ Visualization of "assets to be protected" ■ Learning, analysis, and storage of communication content ■ Anomaly detection and recovery/improvement *For more details, please download the PDF or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
Our company offers one-stop support for PSIRT, including not only the planning of construction but also assistance in the preparation of PSIRT-related documents, security threat and incident analysis, support for obtaining Achilles certification, assessments, training, incident response support, and operational evaluations. Please feel free to contact us if you have any requests. *PSIRT refers to an organization that manages risks related to security vulnerabilities in products manufactured or sold by the company and responds to emergencies during security incidents. While CSIRTs have also become widespread, the difference from CSIRTs is that PSIRTs are security response organizations specifically for IoT products and IoT services provided to customers. [Examples of Services Offered] ■Support for PSIRT construction planning ■Assistance in the preparation of PSIRT-related documents, etc. *For more details, please download the PDF or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration