1~31 item / All 31 items
Displayed results
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
Contact this company
Inquiry Form1~31 item / All 31 items

The ID integration management solution "SyncTrust Identity Manager" can automatically link user information such as ID, password, name, and employee number with AD and cloud services in conjunction with the HR system. This eliminates the need for manual management, allowing for error-free and easy ID management associated with personnel changes and organizational restructuring. 【Features】 ■ Prevents forgetting to delete accounts ■ Compatible with Active Directory ■ Standard workflow functionality included ■ Capable of saving the history of ID creation, changes, and deletions ■ Purely domestically developed software It can solve issues such as "I want to implement cloud services, but registering IDs for all employees is a hassle" and "There have been instances of forgetting to delete licenses for former employees, resulting in unnecessary costs." *For more details about the product, please download the materials. Feel free to contact us as well.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
This document introduces the "SyncTrust ID Card Manager," which addresses the challenges of ID card management. By centrally managing access rights that change due to events such as organizational restructuring and personnel transfers alongside account information, efficient operations are achieved. It can be used as an option of "SyncTrust IM" or as a standalone IDCM. We encourage you to read it. 【Contents (excerpt)】 ■Challenges in ID card management ■What is SyncTrust ID Card Manager (IDCM)? ■Features of SyncTrust ID Card Manager ■Examples of the image after implementing SyncTrust IM and IDCM ■Types of cards and card attributes *For more details, please refer to the PDF document or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
"AccessMatrix UCM" is a privileged ID management solution that enables the application and approval of privileged ID passwords through a web-based workflow. All application and approval histories are saved as logs and provided as audit reports. By centrally managing the passwords of privileged IDs across a diverse range of systems, it significantly enhances security and convenience. 【Features】 ■ Zero impact on servers ■ Equipped with automatic password change functionality ■ Equipped with automatic login functionality ■ Allows for a small start to keep costs down ■ Enables detailed permission granting *For more details, please refer to the PDF document or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
AGC Inc., a leading glass manufacturer representing the world, operates globally in over 30 countries and regions. The company has implemented 'AccessMatrix UCM' to streamline the management of privileged IDs assigned to its own and business partner's information system personnel, while ensuring robust security. With the implementation, when personnel change due to transfers, there is no longer a need to assign multiple privileged IDs to each individual as before, thereby reducing the workload related to applications and permission changes. 【Case Study】 ■Challenges - Multiple privileged IDs were assigned per individual/system. - Responding to audits (submitting evidence and inventory, etc.) was inefficient. - Operational staff were constantly assigned privileged ID permissions. ■Product Implemented - AccessMatrix UCM *For more details, please refer to the PDF document or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
We would like to introduce a case study on the implementation of a product that centralized the management of increasing internal system IDs. At Mitsui Trust Loan & Finance Co., Ltd., the increase in internal systems had made ID/password management a significant burden. To improve efficiency, they transitioned from their traditional single sign-on system to 'AccessMatrix USO'. As passwords are no longer exposed and users no longer need to manage multiple passwords, security has been enhanced. 【Case Study】 ■Challenges - The increase in internal systems made ID/password management a significant burden. ■Implemented Product - AccessMatrix USO *For more details, please refer to the PDF document or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
"Sync Trust Identity Manager" is a package solution that integrates with HR systems to automatically link user information such as ID, password, name, and employee number to AD and cloud services. By eliminating manual ID management tasks, it helps prevent human errors and significantly reduces operational workload. Additionally, Microsoft 365 licenses can be automatically registered and deleted, eliminating the risk of forgetting to revoke licenses for departing employees, thus avoiding unnecessary licensing costs and preventing unauthorized access by former employees. 【Features】 ■ Centralization and automation enable improved operational efficiency ■ Flexibly responds to personnel changes and organizational restructuring ■ Easy to implement and operate at a reasonable cost ■ Standard workflow functionality included ■ Can connect with additional implemented systems via connector functionality ■ Fully developed in-house with complete domestic production *For more details, please refer to the PDF document or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
"AccessMatrix USO" is an ID integration management platform solution that enables login to multiple systems with a single authentication. It supports client-server applications and host-emulation applications that traditional SSO (Single Sign-On) products could not accommodate. There is no need to modify existing applications, and no coding is required. 【Features】 ■ Enables SSO for various applications ■ Supports smart devices ■ Can conceal passwords ■ Can be implemented without impacting existing applications ■ Provides audit reports *For more details, please refer to the PDF document or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
The "SyncTrust ID Card Manager (IDCM)" is an ID card management tool that allows for centralized management by linking personnel information (account information) with access rights associated with cards, as well as statuses such as loss or temporary suspension. It enables the streamlining of inputting account information and setting permissions, making it suitable for workplaces with a large number of employees or those with frequent location changes and transfers. It can also be integrated with the ID unified management solution "SyncTrust Identity Manager." Issuing and deactivating guest cards can be easily managed from the control panel, contributing to the reduction of security hole risks caused by the complexity of input and setting changes. 【To address the following challenges and risks】 ■ Access is granted to areas that should not be accessible. ■ ID cards for employees who have changed departments due to personnel transfers cannot be used immediately. ■ There are no countermeasures in place if an ID card is forgotten. ■ ID card information for employees who have resigned remains unchanged. *For more details, please refer to the materials available for download in PDF format. Feel free to contact us with any inquiries.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
The "SyncTrust(R) Working Time Manager" is a work style reform application that combines entry and exit data from ID cards of access control systems with data from attendance management systems and time cards, enabling the visualization and comparison of this data to accurately grasp and visualize actual attendance conditions. Additionally, by integrating this system with existing access control systems and linking the data, it can be utilized as a data tool that aids in attendance information, transitioning from merely serving as a physical security gate. 【System Configuration Diagram】 ■ Extract the first and last entry and exit (arrival/departure) times of the day from the logs of the access control system. ■ The calendar function displays only the access logs for specified holidays. ■ The extracted and displayed data can be output as a CSV file. ■ The extracted and displayed data can be sent via email. *For more details, please download the PDF or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
By introducing the privileged ID management product "AccessMatrix UCM" (hereinafter referred to as UCM), you can implement the application/approval of privileged ID passwords through a web-based workflow, and all of these histories will be saved as logs. However, there is no functionality to reconcile these logs with the logs of operations performed using privileged IDs. "Log compare for AccessMatrix UCM" is a privileged ID operational management solution that allows you to understand the usage status of privileged IDs and identify privileged IDs that are not managed by UCM by reconciling the logs of UCM with the logs of the systems managed by UCM. 【Main Features】 ■ Detection of unauthorized logins - Use of privileged IDs not managed by UCM ■ Detection of logins outside the designated period - Usage history of privileged IDs that deviated from the application period of UCM ■ Confirmation of logins within the designated period - Usage history during the application period by privileged IDs managed by UCM *For more details, please refer to the PDF materials or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
Abroad, the concept of Wi-Fi security measures that completely prohibits the use of any Wi-Fi other than that authorized by the company has already become widespread. 'AIRTMS' is a solution that realizes such international standards of Wi-Fi security. The sensor itself determines unauthorized Wi-Fi usage and quickly blocks unauthorized connections at high speed. It can be implemented as an independent system separate from the existing network. 【Features】 ■ Instantly (0-4 seconds) shut out unauthorized Wi-Fi usage ■ Block wireless LAN connections that are not under management, such as tethering and portable Wi-Fi routers ■ Prevent security incidents such as malware infections and information leaks ■ Achieve international standards of Wi-Fi security *For more details, please refer to the PDF document or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
Wi-Fi is convenient, but it is difficult to manage due to factors such as "the signals are invisible," "they cannot be identified by appearance," and "it is hard to understand who is doing what." This document introduces the Wi-Fi security sensor 'AIRTMS' that protects companies from threats lurking in the Wi-Fi environment. It includes information on the security risks of Wi-Fi in everyday life, the ideal state in the Reiwa era, steps for utilization, and screen images. We encourage you to read it. [Contents (excerpt)] ■ Wi-Fi is convenient, but... ■ An era where we have no choice but to use Wi-Fi ■ Security risks of Wi-Fi lurking in everyday life ■ Things to be aware of in corporate Wi-Fi security management ■ Unauthorized APs can be easily constructed *For more details, please refer to the PDF document or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
Our company provides security solutions to create a safer business environment. "Are you struggling with traditional security measures like disk encryption and device control being insufficient?" "There are many limitations in file formats and usability with conventional file encryption products." With 'DataClasys', you can encrypt various data on a file-by-file basis, regardless of file format or storage location. Once a file is encrypted, it maintains its original state, minimizing damage in the event of a leak or breach. [Background/Challenges] - The sophistication and cunning of security threats, including targeted attacks - Diversification of devices and services used - Diversification of data (file) storage locations, including on-premises and cloud - Traditional security measures like disk encryption and device control are insufficient - Insufficient risk management in the event of data leakage or breach - Many limitations in file formats and usability with conventional file encryption products *For more details, please refer to the related link page or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
Are you having trouble with things like 'the whereabouts of data (files) containing personal information is uncertain' or 'it's unclear whether the data handling rules are being properly implemented'? Our company provides security solutions to create a safer business environment. With 'P-Pointer File Security', you can quickly search for internal data and identify the location of data containing personal information. It executes necessary processes such as data movement and deletion based on handling rules. [Background/Issues] ■ The whereabouts of data (files) containing personal information is uncertain. ■ It's unclear whether the data handling rules for personal information are being properly implemented. *For more details, please refer to the related link page or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
Are you struggling with issues such as the difficulty in understanding usage situations due to unauthorized access points? Are the measures to prevent attacks and unauthorized access via Wi-Fi insufficient? Our company offers security solutions to create a safer business environment. With 'AIRTMS', you can continuously monitor and visualize Wi-Fi usage. It can detect and block communication from unauthorized access points and unapproved devices. [Background/Challenges] - The increase in the use of mobile devices has led to a rise in Wi-Fi (wireless LAN) usage. - It is difficult to grasp usage situations due to unauthorized access points. - Measures to prevent attacks and unauthorized access via Wi-Fi are insufficient. - The burden of reconstructing existing networks for security measures. *For more details, please refer to the related link page or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
Our company provides security solutions to create a safer business environment. Are you struggling with the increasing burden of managing IDs and passwords as users utilize a diverse range of devices, leading to security issues such as password reuse and inadequate updates? With "WisePoint Shibboleth," you can enhance user authentication through one-time passwords, multi-factor authentication, and multi-step authentication, reducing the risk of unauthorized access due to user impersonation. [Background/Challenges] - Diversification of devices used by each user - Increase in applications and services used - Growing burden of managing IDs and passwords - Decreased security due to password reuse and inadequate updates *For more details, please refer to the related link page or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
Our company provides solutions suitable for customers who feel that "manual responses have limitations." Are you experiencing issues such as "the application/approval flow is complicated and varies by department or system" or "insufficient audit responses for checking and verifying usage"? With 'AccessMatrix UCM', we unify the application/approval and password issuance workflows. It reduces the burden of ID management tasks, such as automatic password updates, and makes it easy to create audit reports, with automation also possible. [Background/Challenges] ■ Managing privileged IDs/passwords manually (by hand) ■ The application/approval flow is complicated and varies by department or system ■ The burden of ID management has increased with the growth of target systems ■ Insufficient audit responses for checking and verifying usage *For more details, please refer to the related link page or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
Are you struggling with issues such as using an old system that cannot manage ID integration and the decline in security due to password reuse?" "Our company provides solutions tailored to our customers, focusing on 'improving operational efficiency,' 'reducing human errors,' and 'strengthening audit compliance.' With 'AccessMatrix USO,' we enhance user convenience through single sign-on (SSO). It offers high security with a proven track record, especially among financial institutions. [Background/Challenges] ■ Many business systems in use (applications, servers) ■ Using an old system that cannot manage ID integration (client/server systems, custom-developed applications, consoles, etc.) ■ Burden on users with different IDs/passwords ■ Decline in security due to password reuse *For more details, please refer to the PDF document or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
Our company provides solutions tailored to our customers, such as "improving operational efficiency," "reducing human errors," and "strengthening audit responses." "Accurate understanding and visualization of attendance status is necessary as part of work style reform." "Are you experiencing an increase in the workload for aggregation, analysis, and report creation?" With 'SyncTrust Working Time Manager,' you can automatically aggregate logs from attendance management and entry/exit management systems. It easily displays statistical graphs and distributes regular reports. [Challenges] ■ Accurate understanding and visualization of attendance status is necessary as part of work style reform. ■ Insufficient linkage between attendance management/entry/exit management and user (employee) information. ■ Increased workload for aggregation, analysis, and report creation. *For more details, please refer to the PDF document or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
"I want to conduct an audit of privileged ID usage history, but I'm looking for something simple." "I want to confirm whether the work done with privileged IDs is being carried out as per the application." Do you have anything like that? Our company provides solutions suitable for customers who feel that "manual responses have their limits." With 'Log compare,' you can match the application data of the privileged ID management solution AccessMatrix UCM with the login data of the target management server and display the matching results simply. [Challenges] ■ I want to conduct an audit of privileged ID usage history, but I'm looking for something simple. ■ I want to confirm whether the work done with privileged IDs is being carried out as per the application. *For more details, please refer to the related link page or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
Our company provides solutions tailored to our customers, such as "improving operational efficiency," "reducing human errors," and "enhancing audit responses." Do you have any needs like "I want to handle tasks like forgetting ID cards, issuing visitor cards, and reissuing them accurately and easily" or "I want to reduce the workload of updating card information"? With 'SyncTrust ID Card Manager,' you can manage permissions for multiple ID cards in bulk. You can also set detailed permissions individually. [Challenges] ■ I want to reduce the workload of updating card information. ■ I want to handle tasks like forgetting ID cards, issuing visitor cards, and reissuing them accurately and easily. ■ I want to link personnel data with ID card management. *For more details, please refer to the PDF document or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
"Is it difficult for you to quickly find the necessary user information among a large number of user details, or is there no easily viewable shared address book that corresponds to your organizational hierarchy?" Our company provides solutions suitable for customers who feel that "manual responses have their limits." With 'SyncTrust Contact', you can immediately use a web-based shared address book, displaying results clearly through keyword and department searches. You can also display user (employee) photo data. [Challenges] ■ Difficulty in quickly finding necessary user information among a large number of user details ■ Lack of an easily viewable shared address book that corresponds to the organizational hierarchy ■ No shared address book that responds in real-time to personnel changes or organizational restructuring *For more details, please refer to the related link page or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
Our company provides solutions suitable for customers who feel that "manual responses have their limits." Are you struggling with issues such as "having many group companies, affiliated companies, and subsidiaries," "frequent organizational changes and personnel transfers," or "complex settings, management, and operations for each system"? With 'SyncTrust Identity Manager,' you can flexibly integrate with various systems and cloud services, including Active Directory and groupware. By automating ID management and application, you can reduce operational burdens and human errors. [Background and Challenges] ■ There are many business systems in use (applications, servers) ■ There is a large number of users ■ There is a huge volume of user support tasks such as password resets ■ Operational rules and management systems are inconsistent ■ It is difficult to grasp the status of user information updates and deletions *For more details, please refer to the PDF document or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration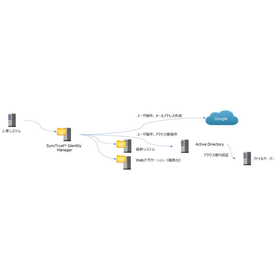
"SyncTrust IM" is an ID and account management solution that automates and streamlines business operations. Company F in the service industry has many group companies and a large number of users to manage, which made account management tasks busy, but they faced the problem of not being able to secure enough personnel for the tasks. Therefore, they implemented our product. This allowed them to manage with fewer personnel, and by appointing administrators for each group company, they were able to reduce the workload. [Case Overview] ■ Implemented Product: SyncTrust Identity Manager ■ Number of Users: Approximately 1,900 ■ Integrated Systems - Active Directory (Windows Server 2008) - G Suite - Core System *For more details, please refer to the PDF document or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
"SyncTrust IM" is an ID and account management solution that automates and streamlines operations. Company E in the manufacturing industry faced issues due to varying HR systems and management methods across its group companies, resulting in a lack of consolidated HR information and an increased workload for organization and management. To address this, the company implemented our product. By standardizing the rules for HR information, they significantly reduced the workload for organizing information. With the company and organizational master data, they were able to automate account operations tailored to their organization. [Case Overview] ■ Product Implemented: SyncTrust Identity Manager ■ Number of Users: Approximately 15,000 ■ Integrated Systems - Active Directory (Windows Server 2008) - Oracle Directory Server - PowerGres Database - Cloud System Integration Tools - Single Sign-On System *For more details, please refer to the PDF document or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
"SyncTrust IM" is an ID and account management solution that automates and streamlines business operations. The Independent Administrative Institution D Organization faced a problem where account information was not centrally managed, making it difficult to properly manage who could log into which systems. To address this issue, our product was implemented. The account management system retains the account information of users registered in each application, allowing for inquiries into account information through searches by username, department name, and more. [Case Overview] ■ Implemented Product: SyncTrust Identity Manager ■ Number of Users: Approximately 600 ■ Integrated Systems - Active Directory (Windows Server 2008R2) - Mail Server (Postfix+Dovecot) - IC Card Management Server (SecureDive) - General Affairs System - Groupware (WebAS Key’s Portal) *For more details, please refer to the PDF document or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
"SyncTrust IM" is an ID and account management solution that automates and streamlines operations. In the central government organization C, the management of staff was entrusted to certain users within each organization, and the management of accounts for information systems was not centralized. Therefore, this product was introduced. By delegating account management authority to users performing operations and providing an easy-to-understand web interface, centralized management of accounts has become possible. [Case Overview] - Product Introduced: SyncTrust Identity Manager - Number of Users: Approximately 74,000 - Integrated Systems: - Active Directory (Windows Server 2008 R2) - Microsoft Exchange Server 2013 - FileZen *For more details, please refer to the PDF document or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
"SyncTrust IM" is an ID and account management solution that automates and streamlines business operations. Company B in the service industry had a request to securely access internal content from outside the company and to integrate it with employee ID cards to consider potential loss. As a result, this product was implemented. With the one-time password solution from IP Cube, secure access has been achieved. [Case Overview] ■ Implemented Product: SyncTrust Identity Manager ■ Number of Users: Approximately 1,000 ■ Integrated Systems - Active Directory (Windows Server 2012R2) - Microsoft Exchange Server 2013 - RADIUS Server (Enterpras) - One-Time Password (AuthWay) - SSL-VPN (Appliance) *For more details, please refer to the PDF document or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
"SyncTrust IM" is an ID and account management solution that automates and streamlines business operations. Company A in the service industry faced challenges due to the large number of systems they managed and frequent personnel changes occurring almost every month, making account creation for each system difficult and problematic. With the introduction of our product, it has become automatically linked to the information from the HR system, resulting in almost no maintenance work related to account management. [Case Overview] ■ Product Implemented: SyncTrust Identity Manager ■ Number of Users: Approximately 15,000 ■ Linked Systems - CP Messaging Server (Our handled mail server) - CP Directory Server (Our handled LDAP server) - Active Directory (Windows Server 2012R2) - Oracle Database 11g *For more details, please refer to the PDF document or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
"SyncTrust IDCM" enables efficient operations by centrally managing access rights that change during events such as organizational restructuring and personnel transfers alongside account information. Company G in the manufacturing industry was manually inputting personnel information into their ID card management system, resulting in a significant increase in labor hours. Therefore, they implemented our product. By greatly reducing the management tasks for system IDs and ID cards, they were able to replace the old system while keeping personnel costs lower. [Case Overview] - Implemented Product: SyncTrust ID Card Manager - Challenges/Issues Before Implementation: - The labor hours for the ID card management system were very high. - Due to the complexity of the registration process to Active Directory (AD), they considered a system that could reduce workload and enable ID integration with the ID card management system. - The ID card management system was outdated, and maintenance costs were high, prompting a consideration for replacement. *For more details, please refer to the PDF document or feel free to contact us.*
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration
"Log compare" is a solution that simply matches server login information with privileged ID application information. Company H in the service industry manages dozens of Windows Servers and had been conducting maintenance using privileged ID management, but they were unable to check whether the work was being carried out according to the application information. Therefore, they implemented our product. By matching the logs of Windows Servers with the application logs from AccessMatrix UCM, they were able to display and verify the matching results in a simple and easy-to-understand manner. [Case Overview] ■ Implemented Product: Log compare ■ Effects After Implementation - Matched application logs, allowing for simple and clear display and verification of matching results. - It became possible to provide matching data as proof for the auditing tasks that had been a challenge. *For more details, please refer to the related link page or feel free to contact us.
Added to bookmarks
Bookmarks listBookmark has been removed
Bookmarks listYou can't add any more bookmarks
By registering as a member, you can increase the number of bookmarks you can save and organize them with labels.
Free membership registration